Tr0ll 2
IN PROGRESS 15 Dec 2015 VulnHub
After completing the first boot2root in the tr0ll series, I decided to try my luck on the second. I booted up the vm and ran the command arp-scan –localnet to find out the IP address. I than ran an nmap scan (nmap -sS -A 192.168.116.154) to see what services were running.
Like the last tr0ll vm, I decided to start my analysis on port 80. I opened up Firefox and and shot over to 192.168.116.154. Again, I see the all to familiar meme face.
Nothing too suspicious here after viewing the webpage’s source code. I was met with the message Nothing here, Try Harder!, with Try Harder! being a common montra found in the OSCP courses.
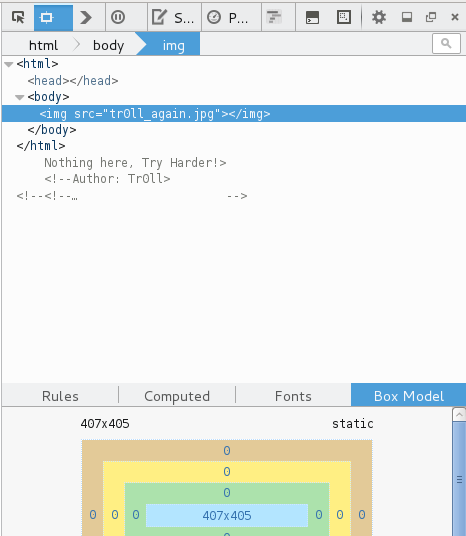
The next thing I looked for was a robots.txt file to see if there were any directories a “spider shouldn’t be allowed” to crawl. I found a list of potential directories to visit.
The first directory called noob displayed the following image. I felt like I was going to be noticing a pattern with the following directories to come.
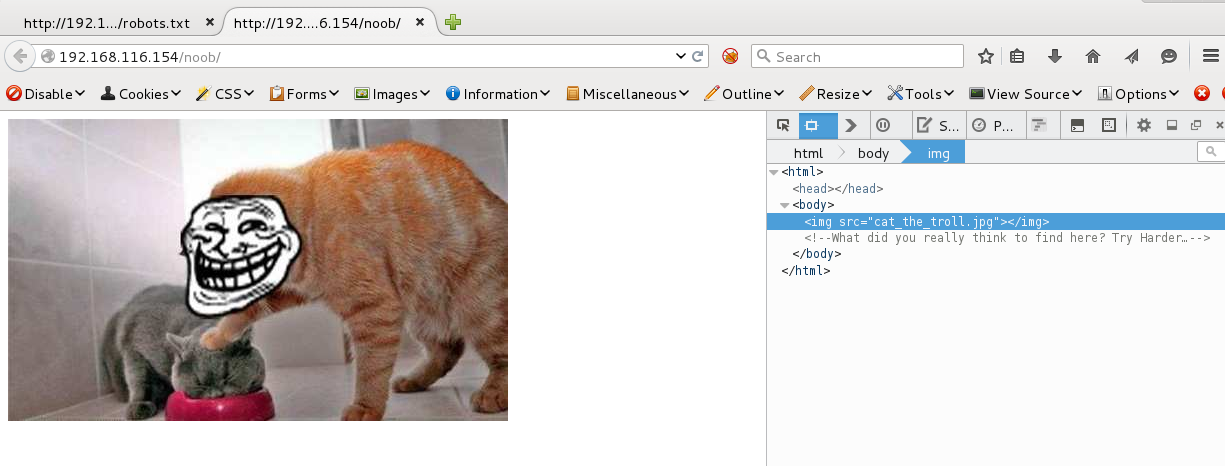
The next two directories, nope and try harder came back 404, but the fourth called keep trying displayed the same familiar image as noob. After looking through the rest of the directories, two more came back with the same image, don’t bother and ok this is it. Nothing looked suspicious in the source code, so I decided to take a look at the images themselves. Perhaps stegonography is being used?? I downloaded all four of the images and each came back at 15.8kb except for the image from the directory dont bother which had a size of 15.9kb.
From here I decided to try using the command strings to see if any human readable txt could be grabbed from the picture.

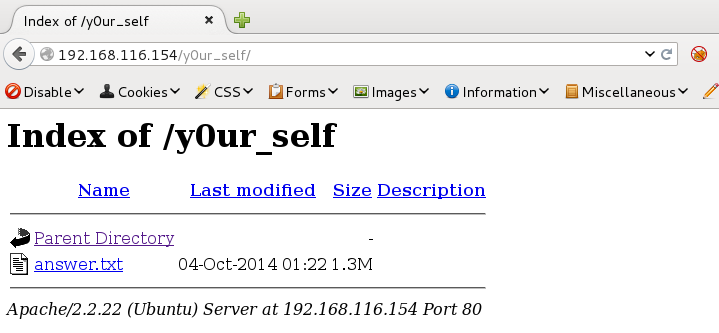
“Look Deep within y0ur self for the answer.” From the misspelling of y0ur, I assumed that y0ur self was a directory. When appending it to the end of the domain (192.168.116.154), the following page was displayed
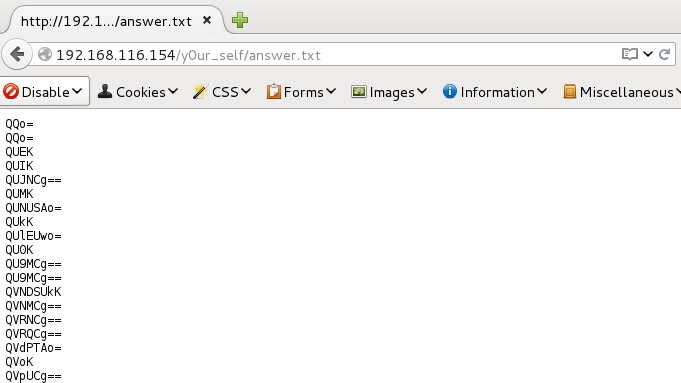
When opening the text file answers.txt I was presented with a huge list of strings that were base64 encoded as indicated by the “==” at the end of some of the strings.
I ran the following command to decode the entire list and write it out to the text file output.txt.
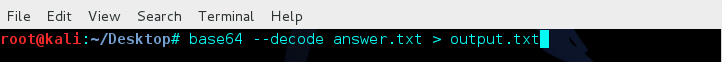
Now I had a huge list of human-readable strings, which I assumed were going to help me get access through ftp or ssh. I decided to start with ftp first, by using the list along with Hyrda to bruteforce the username and password. Only 9 billion possible combinations to try… Using the command below, I used output.txt as a list to test against the username and password.
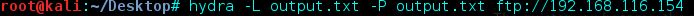
32 hours to test all possible combinations… I started to think I wasn’t going about this the way. Maybe the list only contains possible passwords and the username is static?
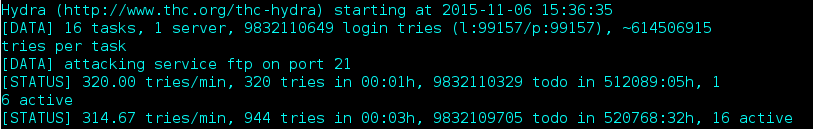
In the first tr0ll vm, when I used hydra to bruteforce ssh, I had one constant for the password and a list to test for usernames. I had a feeling tr0ll2 took a similar approach. Looking back at output.txt, I noticed that many of the strings were common names. I