Bandit
COMPLETE 25 Dec 2015 OverTheWire
Now that I’ve completed my first boot2root (tr0ll) I decided to start looking at some different websites I could practice my skills on. One site I kept hearing about was overthewire.org so I finally checked it out. It recommended that I begin with the Bandit war game, so I will keep this post updated as a progress through the different levels of Bandit.
BANDIT LEVEL 0
Level 0 Goal: The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
Commands: ssh

What I Did: ssh into the home directory. List file using ls and then used cat to see what the file held.
Level 1 Password: boJ9jbbUNNfktd78OOpsqOltutMc3MY1
BANDIT LEVEL 1
Level 1 Goal: The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH. Whenever you find a password for a level, use SSH to log into that level and continue the game.
Commands: ls, cd, cat, file, du, find

What I Did: ssh into the home directory. Since ”-“ is a special character, you need to use the command cd_ _./- in order to see the password for level 2.
Level 2 Password: CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
BANDIT LEVEL 2
Level 2 Goal: The password for the next level is stored in a file called spaces in this filename** located in the home directory
Commands: ls, cd, cat, file, du, find
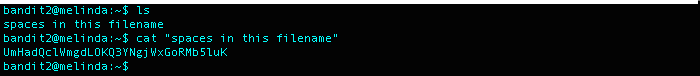
What I Did: ssh into the home directory. Used cat and then added double quotes (“ “) to escape the spaces in the filename.
Level 3 Password: UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
BANDIT LEVEL 3
Level 3 Goal: The password for the next level is stored in a hidden file in the inhere directory.
Commands: ls, cd, cat, file, du, find
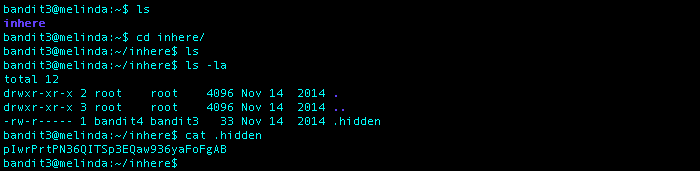
What I Did: cd into the directory inhere. Used the command ls -a so that hidden files were shown. Then used the cat command on the file .hidden to see the password for level 4.
Level 4 Password: pIwrPrtPN36QITSp3EQaw936yaFoFgAB
BANDIT LEVEL 4
Level 4 Goal: The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
Commands: ls, cd, cat, file, du, find
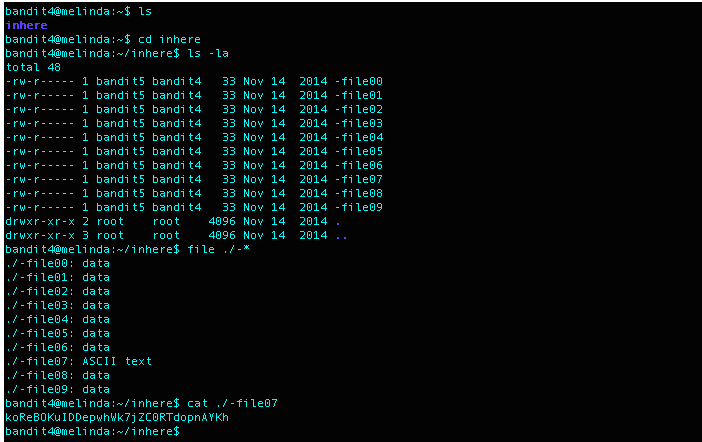
What I Did: cd into the inhere directory and used the file command on all files in the directory which indicated that ./-file07 contained ASCII text which indeed held the password for level 5.
Level 5 Password: koReBOKuIDDepwhWk7jZC0RTdopnAYKh
BANDIT LEVEL 5
Level 5 Goal: The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties: human-readable - 1033 bytes in size - not executable
Commands: ls, cd, cat, file, du, find
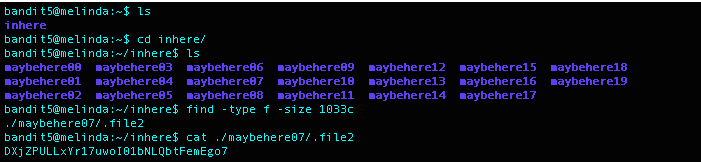
What I Did: used ls to see what directories and files were in the directory inhere. Used the command find -type f -size 1033c to find the file that met the properties mentioned above. Used the cat command on the returned output which was ./maybehere07/.file2 and was returned the password for level 6.
Level 6 Password: DXjZPULLxYr17uwoI01bNLQbtFemEgo7
BANDIT LEVEL 6
Level 6 Goal: The password for the next level is stored somewhere on the server and has all of the following properties: owned by user bandit7 - owned by group bandit6 - 33 bytes in size
Commands: ls, cd, cat, file, du, find, grep
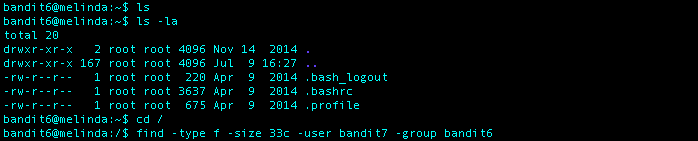
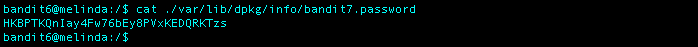
What I Did: Nothing showed up in the first directory I was logged into, so I decided to cd into the root (/) directory. I than ran the command find -type f -user bandit7 -group bandit6 -size 33c which met most of the properties mentioned in the level 6 goals. The result that caught my eye right away was ./var/lib/dpkg/info/bandit7.password. I used the cat command on the file and was given the password for level 7.
Level 7 Password: HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
BANDIT LEVEL 7
Level 7 Goal: The password for the next level is stored in the file data.txt next to the word millionth
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
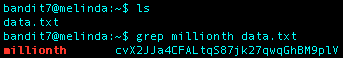
What I Did: Was given a text file called data.txt and needed to find the password for the next level, which was next to the word millionth. I used the command grep “millionth” data.txt and was returned the searched word with the password for level 8 next to it.
Level 8 Password: cvX2JJa4CFALtqS87jk27qwqGhBM9plV
BANDIT LEVEL 8
Level 8 Goal: The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
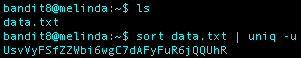
What I Did: This level was pretty straight forward. First I used the sort command on data.txt and appended uniq -u to search for a uniq line in the file.
Level 9 Password: UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
BANDIT LEVEL 9
Level 9 Goal: The password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ‘=’ characters.
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
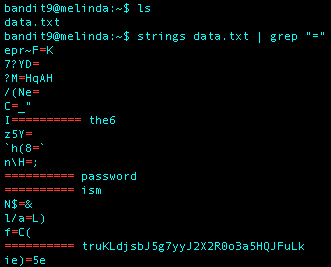
What I Did: Used strings on data.txt and appended grep ’=’ to print all strings in the file beginning with ’=’
Level 10 Password: truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
BANDIT LEVEL 10
Level 10 Goal: The password for the next level is stored in the file data.txt _,which contains base64 encoded data.
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
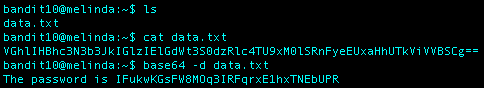
What I Did: This level was really easy. Just used the command base64 -d data.txt to decode the base64 encoded data. The output was “The password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR”
Level 11 Password: IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
BANDIT LEVEL 11
Level 11 Goal: The password for the next level is stored in the file data.txt ,where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
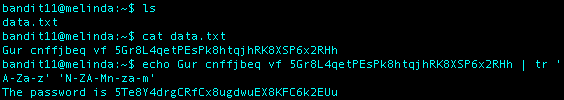
What I Did: After using cat on data.txt I received a string that had a ROT13 cipher applied to it. After reading up on ROT13, I discovered that the same cipher is used to encode and decode a string. Using the command echo on the encrypted string and appending tr ‘A-Za-z’ ‘N-ZA-Mn-za-m’ to the command, the encrypted string was decoded resulting in the output of “The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu”
Level 12 Password: 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
BANDIT LEVEL 12
Level 12 Goal: The password for the next level is stored in the file data.txt ,which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp and rename it using mv (read the manpages!)
Commands: grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd, mkdir, cp, mv
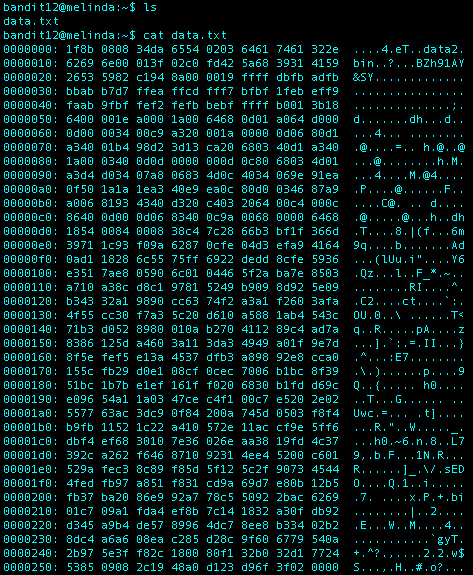
What I Did: This level sucked. Had to look up a hint because I was unsure what to do once I converted the hexdump using xxd. First thing I did was output the results of the xdd conversion to the directory /tmp/output as a.txt (you need to make the directory first using the mkdir command). Once I used the cat command, I could see that that I was still working with a compressed file.
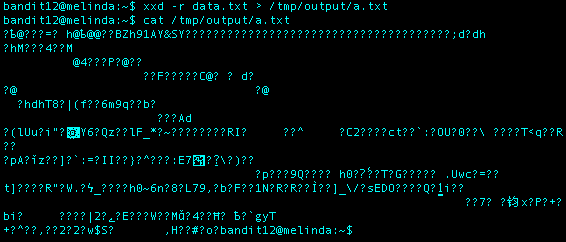
Using the file command, I could see I was working with gzip compressed data. I renamed the file a.txt to a.txt.gz so I could decompress the file using gzip.
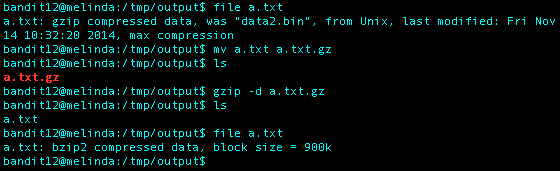
Once decompressed, I ran the file command again and saw I working with bzip2 compressed data with a block size = 900k. Ok, I renamed a.txt to a.txt.bz2 so I could decompress the file using bzip2.
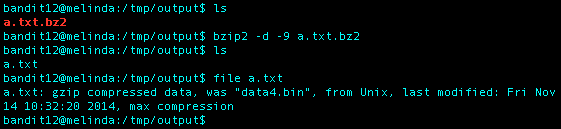
Back to working with gzip again. I followed the same gzip process shown above and used the file command on the file again and received the following:
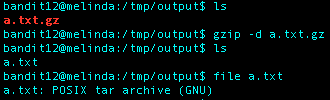
Now, I was working with a tar file. I renamed a.txt to a.txt.tar and decompressed using the tar xf command.
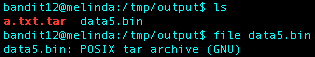
I extracted the file data5.bin and ran the file command again to see it was also a POSIX tar archive. Using the same process as above, I received the following:
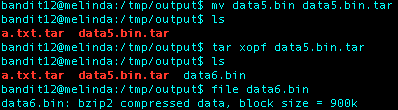
Getting old now… Used the bzip2 process I’ve done multiple times…
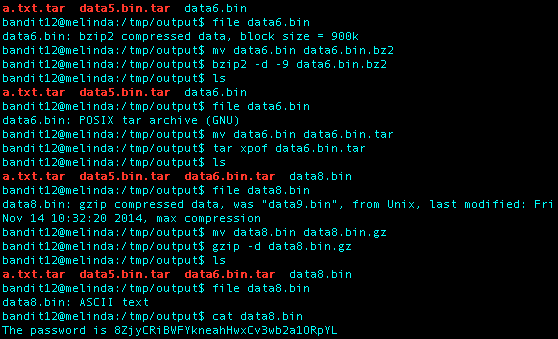
I continue this decompression mess using the various bzip2, gzip, and tar methods until I finally end up with a file called data8.bin with a file type being ASCII txt. I ran the cat command on the file and ended up with the string “The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL”.** What an annoying level…
Level 13 Password: 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
BANDIT LEVEL 13
Level 13 Goal: The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on.
Commands: ssh, telnet, nc, openssl, s_client, nmap
What I Did: Once connected to bandit13, I could see I needed to utilize a private ssh key called sshkey.private to connect to bandit14. I used FileZilla to grab the key (couldn’t get scp to work for whatever reason), I then used the command ssh -i sshkey.private bandit14@bandit.labs.overthewire.org. It gave some error saying I shouldn’t be using shared private keys or something. I just appended sudo to the beginning of the command to see if I could override the error, which I was able to successfully do.
Level 14 Password: private ssh key to login
BANDIT LEVEL 14
Level 14 Goal: The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
Commands: ssh, telnet, nc, openssl, s_client, nmap
What I Did: Pretty straightforward. Copied down the password and use the command telnet to open a connection and typed in open localhost 30000 to specify the connection is on port 30000. Then I just typed in 4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e and was presented with the password for Bandit15.

Level 15 Password: BfMYroe26WYalil77FoDi9qh59eK5xNr
BANDIT LEVEL 15
Level 15 Goal: The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Helpful note: Getting “HEARTBEATING” and “Read R BLOCK”? Use -quiet and read the “CONNECTED COMMANDS” section in the manpage. Next to ‘R’ and ‘Q’, the ‘B’ command also works in this version of that command…
Commands: ssh, telnet, nc, openssl, s_client, nmap
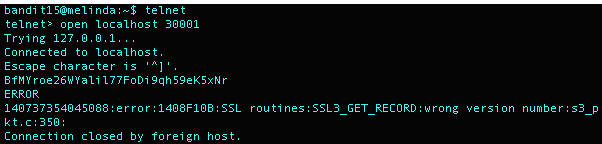
What I Did: Wanted to see what would happen if I used the process for Bandit14 on Bandit15. I knew it was most likely not going to work and I received the following error message:
ERROR
140737354045088:error:1408F10B:SSL routines:SSL3_GET_RECORD:wrong version number:s3_pkt.c:350:
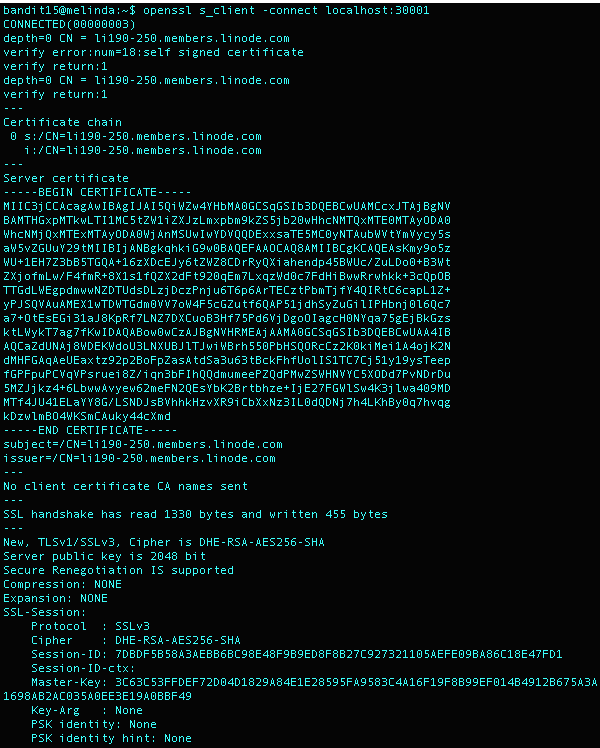
I then looked up ways for telnet to communicate over ssl and found that OpenSSL has an SSL tool. Using the command openssl s_client -connect localhost:30001 I procured the following output.
I then tried to pass the Bandit15 password and received the following output…
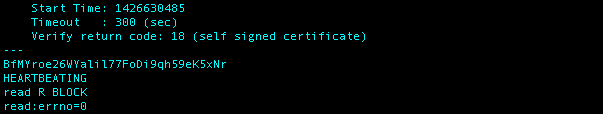
I was receiving the errors warned about in the level goal, so that some good news. I appended -quiet to the end of the command to look like openssl s_client -connect localhost:30001 -quiet and once I entered the Bandit15 password, I received the following output.
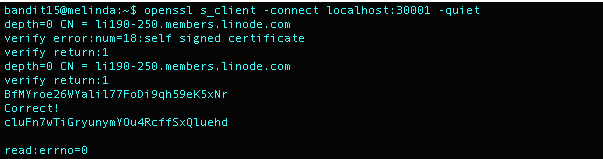
Level 16 Password: cluFn7wTiGryunymYOu4RcffSxQluehd
BANDIT LEVEL 16
Level 16 Goal: The password for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next password, the others will simply send back to you whatever you send to it.
Commands: ssh, telnet, nc, openssl, s_client, nmap
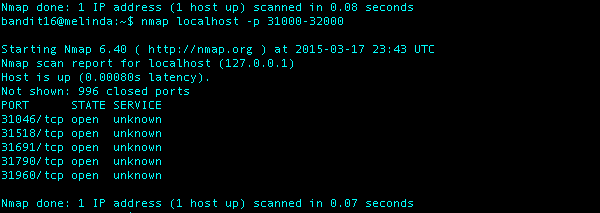
What I Did: Using nmap I ran a scan on all the ports between 31000 and 32000 and got back results that 5 were open. From here it was just trial and error using the previous command from Bandit16 openssl s_client -connect localhost:(testing each port number shown in the picture above). Port 31790 returned the response shown below when I entered the password for Bandit16.
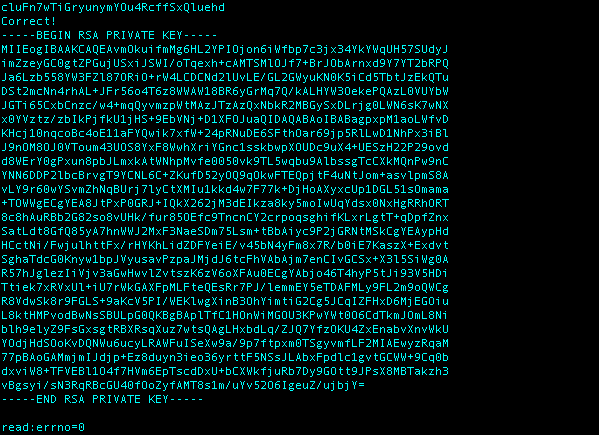
I took this RSA Private Key and copied it to a file called Bandit17 because I knew I was going to have to do a private key login similar to Bandit14. I created a file in /tmp called ssh.private and copied the RSA into it using nano. I then changed the permissions using chmod 600 and finally gained a shell on Bandit17 using the command ssh -i ssh.private bandit17@localhost
Level 17 Password: RSA Private Key shown above
BANDIT LEVEL 17
Level 17 Goal: There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
NOTE: If you have solved this level and see ‘Byebye!’ when trying to log into bandit18, this is related to the next level, bandit19.
Commands: cat, grep, ls, diff
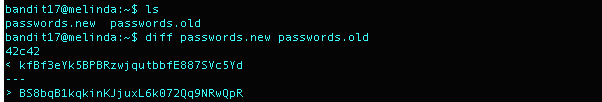
What I Did: Ran the command diff between the two files and found the line that was changed. The top line has the password we want to use for Bandit18.
Level 18 Password: kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
BANDIT LEVEL 18
Level 18 Goal: The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified the .bashrc to log you out when you log in with SSH.
Commands: ssh, ls, cat
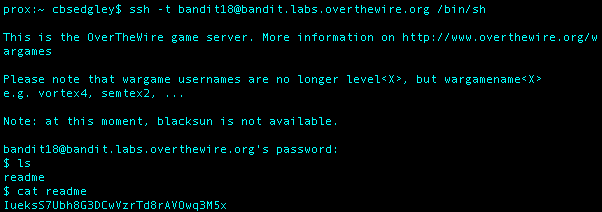
What I Did: Used the command ssh -t bandit18@bandit.labs.overthewire.org /bin/sh to spawn a shell through a pseudoterminal which would bypass the .bashrc file logging the user out.
Level 19 Password: IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
BANDIT LEVEL 19
Level 19 Goal: To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
Commands: none provided in this level
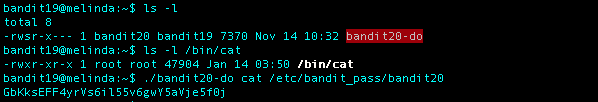
What I Did: finish
Level 20 Password: GbKksEFF4yrVs6il55v6gwY5aVje5f0j
BANDIT LEVEL 20
Level 20 Goal: There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: To beat this level, you need to login twice: once to run the setuid command, and once to start a network daemon to which the setuid will connect.
NOTE 2: Try connecting to your own network daemon to see if it works as you think
Commands: ssh, nc, cat


What I Did: Another straight forward level. Used the command nc -l -p 1234 to start a server on localhost listening on port 1234. I then used the command ./suconnect 1234 to make the connection to the localhost. Once both the listening port and connection was made, I then sent the password from Bandit20 and was returned the password for Bandit21.
Level 21 Password: gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
BANDIT LEVEL 21
Level 21 Goal: A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Commands: cron, crontab, crontab(5) (use “man 5 crontab” to access this)
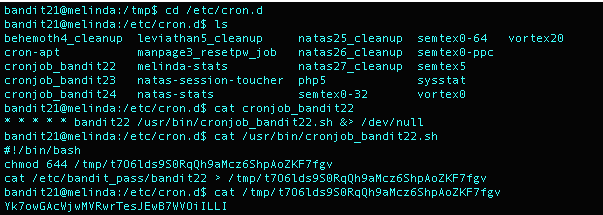
What I Did: I used the command cd to see what cronjobs were running in the directory /etc/cron.d. I found one called cronjob_bandit22 ,which I figured was the one I wanted to look at. Using the cat command, I could see that it was running a script called cronjob_bandit22.sh in the directory /usr/bin. After using the cat command on the script, I could see that the script took the password stored in the file /etc/bandit_pass/bandit22 and output the results to a file in the tmp directory called t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv. Once I used the cat command on the file, I received the password for Bandit22.
Level 22 Password: Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
BANDIT LEVEL 22
Level 22 Goal: A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
Commands: cron, crontab, crontab(5) (use “man 5 crontab” to access this)
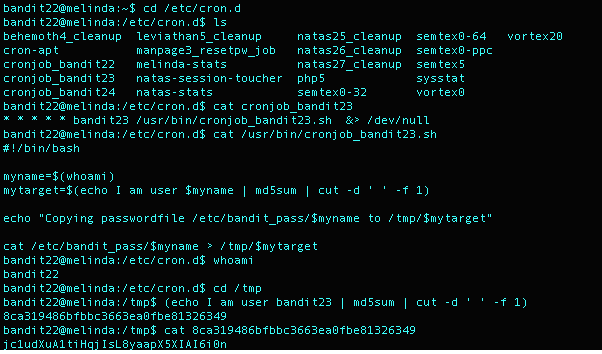
What I Did: Again, I checked out the cronjobs running in the directory /etc/cron.d. My target this time was clearly cronjob_bandit23. A quick cat of the cronjob told me that it ran the script cronjob_bandit23.sh under the directory /usr/bin. Using the cat command again I saw that it stored the password for Bandit23 in a file that was a md5 has of the following information: echo I am user $myname “append” md5sum “append” cut -d ’ ‘ -f 1. I replaced the $myname with bandit23 and was returned the following ASCII file: 8ca319486bfbbc3663ea0fbe81326349. I then used the cat command on /tmp/_8ca319486bfbbc3663ea0fbe81326349 and was returned the password for Bandit23.
Level 23 Password: jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
BANDIT LEVEL 23
Level 23 Goal: A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
Commands: cron, crontab, crontab(5) (use “man 5 crontab” to access this)
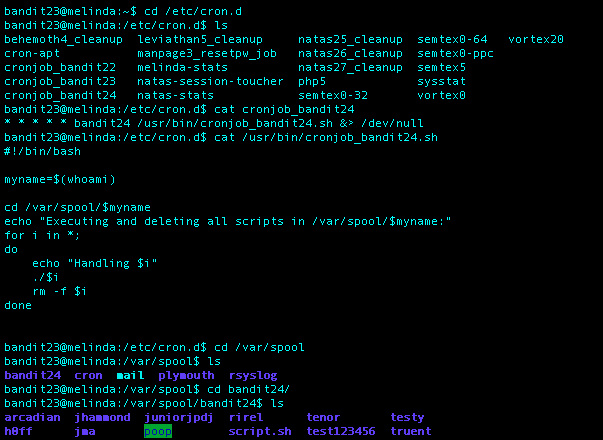
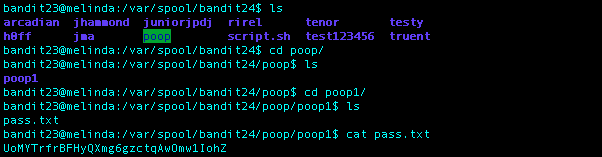
What I Did: Found the password in a file under the directory poop/poop1 called pass.txt. Going to redo this one eventually creating the script like I was supposed to haha.
Level 24 Password: UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ